Cybersecurity is no longer optional. With rising threats like ransomware, phishing, and insider attacks, businesses often ask:
👉 Should I invest in a firewall or endpoint security (EPS)?
The answer: both are essential — but they serve different purposes. Let’s break it down.
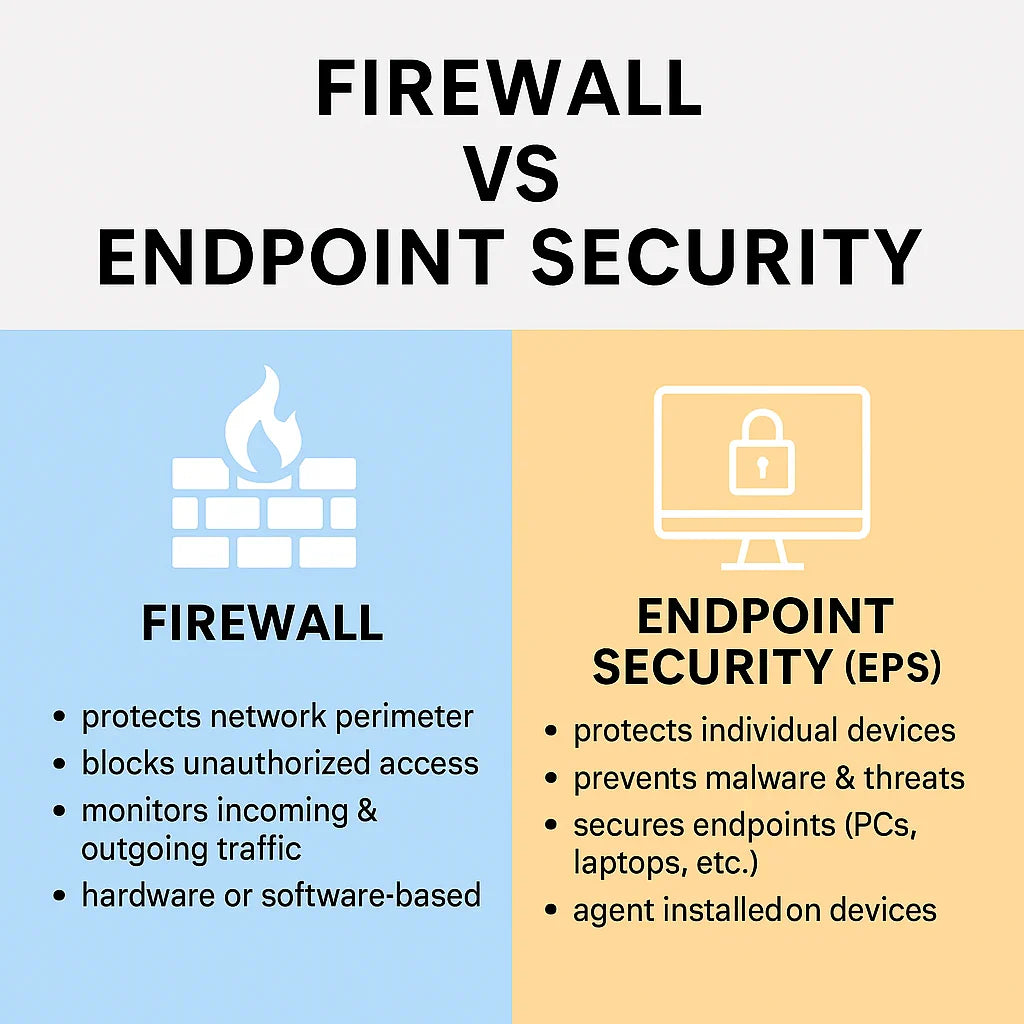
🔒 What is a Firewall?
A firewall acts as a security barrier between your private network and the outside world. It controls data packets (the small chunks of information moving across networks) based on security rules.
Key Features of a Firewall
-
Traffic Filtering – Blocks or allows connections based on rules (IP, port, protocol).
-
Intrusion Prevention – Detects and stops suspicious traffic (DDoS, port scans).
-
VPN Support – Securely connects remote users to the corporate network.
-
Application Control – Manages which apps can use the internet (e.g., blocking torrents).
-
Hardware & Software Options – Can be a physical appliance (e.g., Fortinet, Sophos) or software (Windows Firewall).
👉 Analogy: Think of a firewall as the main gate of a housing society – it checks who can enter and who is blocked.
🖥️ What is Endpoint Security (EPS)?
Endpoint Security (EPS) protects individual devices like PCs, laptops, mobile phones, and servers that connect to the network. Even if a hacker passes through the firewall, EPS ensures your endpoints stay safe.
Key Features of EPS
-
Antivirus/Anti-Malware – Detects and removes viruses, ransomware, spyware.
-
Device Control – Restricts USB, printers, and removable media to prevent data theft.
-
Data Loss Prevention (DLP) – Stops sensitive files from being copied or shared.
-
Patch Management – Ensures endpoints are updated with latest security patches.
-
Centralized Console – Admins can monitor all endpoints from one dashboard.
👉 Analogy: EPS is like giving every resident of the society their own bodyguard – protection even inside the gate.
⚖️ Firewall vs EPS – Side-by-Side Difference
| Aspect | Firewall | Endpoint Security (EPS) |
|---|---|---|
| Scope | Protects the entire network perimeter | Protects individual devices (PCs, laptops, servers) |
| Deployment | Hardware appliance (Fortinet, Sophos) or software | Software agent installed on each endpoint |
| Focus | Blocks unauthorized external access | Prevents malware, phishing, and insider threats |
| Threat Coverage | Network-based threats (hacking, port scanning, unauthorized access) | Device-based threats (viruses, ransomware, data theft via USB) |
| Visibility | Sees traffic patterns and IP behavior | Sees user activity and device-level risks |
| Response | Stops attack before entering network | Stops attack if it reaches a device |
| Example Use Case | Blocking hackers from entering your office network | Preventing employees from copying data on a USB drive |
| Best Fit | Companies needing secure internet access & remote connections | Businesses needing endpoint compliance & malware protection |
✅ Why You Need Both Firewall + EPS
Relying on only one is risky. Here’s why:
-
Firewall Alone: Cannot stop malware from infected USB drives, phishing emails, or insider threats.
-
EPS Alone: Cannot block attackers scanning your network or prevent brute-force login attempts.
👉 Together, they create a layered defense (network + device level).
📌 Real-Life Example
-
Case 1: A hacker tries to access your office server → Firewall blocks unauthorized entry.
-
Case 2: An employee unknowingly downloads a ransomware file via email → EPS stops malware execution.
Both scenarios require different protection layers.
🎯 Final Verdict
-
Firewall = First Line of Defense (Network Gatekeeper)
-
EPS = Last Line of Defense (Device Bodyguard)
-
Combined = Complete Security for businesses and individuals
At Manpra, we provide both Enterprise Firewalls (Fortinet, Sophos, Seqrite) and Endpoint Security solutions (Quick Heal EPS, Seqrite EPS) – ensuring you never have to compromise on protection.